上一篇文章我们实现了自动化qkview的上传,上传之后,我们可以利用脚步执行自动化的诊断提取工作,其工作思路是
-分析并列表当前用户下所有qkview id
-等待用户输入需要分析的qkview id
-执行分析,并输出诊断结果
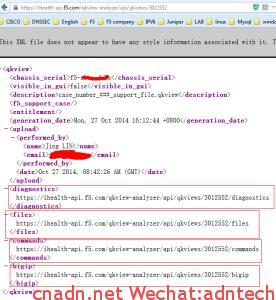
你可以修改脚本做更多的工作,例如输出qkview所采集到的tmsh,linux等相关命令的输出,也可以输出某个指定的文件,只要分析下图中不同的输出即可:
脚本下载:
[wpdm_file id=1]
如何获得下载密码,请微信关注 F5技术 订阅号后,回复downloadpwd
或微信扫描立刻关注
用法:
1.首先应确保你的系统安装了 xmlstarlet 这个命令行xml分析工具。在ubuntu系统下执行
apt-get install xmlstarlet 安装即可
脚本中有如下定义:
XMLPROCESSOR=/usr/bin/xmlstarlet
根据你系统环境的不同,请对应修改执行文件所在位置。
注意:此脚本暂时不支持json格式输出的分析,脚本中用到的jq可不安装,执行时也不要使用参数指定json格式。
2. 运行
ubuntu# USER=Yourihealthname PASS=Yourihealthpwd ./diagnostic-summary.sh
输出类似:
Authenticating
Authentication successful
Currently you have:
***Note: If you see qkview id=0, and SN isf5-abcd-efgh, this mean you not upload qkview yet. 0 is the default and hidden qkview of the system!***3012552 f5-sbuo-dwbs||case_number_###_support_file.qkview|Generation date|Mon, 27 Oct 2014 16:12:44 +0800|Upload date|Oct 27 2014, 08:42:26 AM (GMT)
3012476 f5-sbuo-dwbs||case_number_###_support_file.qkview|Generation date|Mon, 27 Oct 2014 16:12:44 +0800|Upload date|Oct 27 2014, 08:26:09 AM (GMT)Please input a qkview ID that you want to diagnose:3012552
H441024 : LOW : http://support.f5.com/kb/en-us/solutions/public/5000/500/sol5532.html
Log levels are not set to the default value====================================================================================================================
H484499 : HIGH : http://support.f5.com/kb/en-us/solutions/public/15000/700/sol15702.html
SSLv3 vulnerability CVE-2014-3566====================================================================================================================
H431746 : MEDIUM : http://support.f5.com/kb/en-us/solutions/public/11000/800/sol11880.html
BIG-IP objects configured on a different subnet than the self IP address do not send gratuitous ARP requests on failover====================================================================================================================
H638394-23 : MEDIUM : http://support.f5.com/kb/en-us/solutions/public/13000/900/sol13905.html
Log messages report TCL runtime errors====================================================================================================================
H683183 : LOW : http://support.f5.com/kb/en-us/solutions/public/2000/100/sol2167.html
An HTTP monitor send string does not end with the required CR/LF sequence====================================================================================================================
H383290 : LOW : http://support.f5.com/kb/en-us/solutions/public/8000/100/sol8153.html
Unsupported hardware components are used on the system====================================================================================================================
H726514 : LOW : http://support.f5.com/kb/en-us/solutions/public/10000/200/sol10240.htmlhttp://support.f5.com/kb/en-us/solutions/public/3000/100/sol3122.html
The 'ntpq -pn' command reports that there are not enough working NTP servers configured to provide reliable service====================================================================================================================
H415950 : LOW :
VLANs without self IP addresses are present in this BIG-IP system's configuration====================================================================================================================
H770025 : MEDIUM : http://support.f5.com/kb/en-us/solutions/public/15000/300/sol15335.html
The configuration may contain unused objects====================================================================================================================
H686710 : LOW : http://support.f5.com/kb/en-us/solutions/public/10000/000/sol10062.html
The /var/core directory contains core files====================================================================================================================
H638394-7 : MEDIUM : http://support.f5.com/kb/en-us/solutions/public/7000/000/sol7066.html
VLAN failsafe is enabled on a VLAN with no defined interface or self IP address====================================================================================================================
H830235 : MEDIUM : http://support.f5.com/kb/en-us/solutions/public/7000/900/sol7964.html
Cookie or universal persistence may fail for subsequent requests on Keep-Alive HTTP connections====================================================================================================================
H380432 : HIGH : http://support.f5.com/kb/en-us/solutions/public/10000/200/sol10261.htmlhttp://support.f5.com/kb/en-us/solutions/public/13000/400/sol13426.html
Log messages report an excessive number of login failures====================================================================================================================
H479424 : HIGH : http://support.f5.com/kb/en-us/solutions/public/15000/600/sol15605.html
XML Entity Injection vulnerabilities CVE-2014-6032 and CVE-2014-6033====================================================================================================================