如果一个企业希望当用户访问任意SSL加密的数据时也能监控其内容的话,同时又希望用户不要觉察到TA可能在被监控(至少对于绝大部分普通用户来说),可以考虑使用SSL forward proxy。该功能的基本原理类似于前段时间某强大的传说中的火墙干的那样,当请求通过时候,实时on-fly签发一张让用户感觉不到的server证书,这样客户端SSL实际是和中间设备(F5)在通信,F5在server侧模拟充当普通客户与实际网站通信,从而实现数据解密。
对于F5来说,其实际通信过程如下:
- client 发起 client hello 到VIP
- F5 vip接到该client hello后在client侧暂时hold住,不处理
- 同时在server侧发起一个新的SSL会话,通过该会话获得实际服务器的server证书
- 利用server证书里的一些关键信息(CN或者SAN),通过在F5上配置的一个CA实时签发一张关于该server的证书
- F5在client侧回复server hello,以及实时签发的证书给client,最后client侧SSL会话建立
- client 发送实际数据,F5可以看到该实际数据
- F5在server侧利用server侧的SSL会话重新封装数据
如果此时并不想对所有网站都进行这样处理,比如对到一些敏感网站(例如个人网银等)请求,则需要对这些网站进行bypass,所谓bypass就是不让F5获得敏感数据,F5将执行类似纯数据包转发,这个bypass情形的过程如下(假设需求是:缺省截取但对部分网站bypass):
- client 发起 client hello 到VIP
- F5 vip接到该client hello后在client侧暂时hold住,不处理
- 同时在server侧发起一个新的SSL会话,通过该会话获得实际服务器的server证书
- 利用server证书里的一些关键信息(CN或者SAN)或L3、4层信息,查找匹配bypass列表,然后执行下面蓝色或者红色的过程:
- 如果发现匹配,则重新建立一个新TCP连接,将第1步收到的client hello转发给server,后续client和server间的数据,F5只做简单转发。
- 如果没有发现匹配,则执行下面的 7-10过程
- 利用server证书里的一些关键信息,通过在F5上配置的一个CA实时签发一张关于该server的证书
- F5在client侧回复server hello,以及实时签发的证书给client,最后client侧SSL会话建立
- client 发送实际数据,F5可以看到该实际数据
- F5在server侧利用server侧的SSL会话重新封装数据
配置方法:
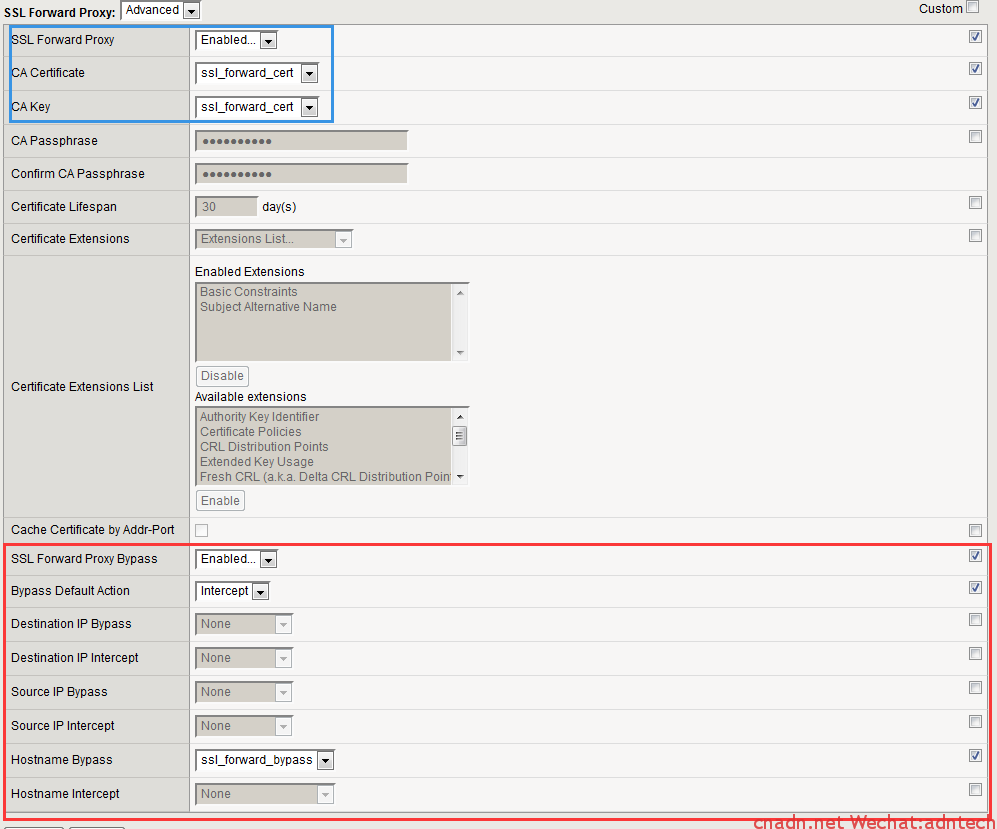
1.配置一个client ssl profile,启用ssl forward proxy:
蓝色是必配部分,而且如果要做的完美(客户端不容易发现的话,这里的CA是关键,得用浏览器能认得)
红色部分为当需要bypass时配置,其中可以配置根据多重条件bypass,具体看在线帮助,配置选项可以直接选择调用data group配置。
2. 配置一个server ssl profile,同样启用ssl forward proxy,另外如果启用bypass的,则必须在client和server 这两个SSL profile中同时启用。
测试效果:
1。没有被bypass,即可以观察明文数据情形:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 |
root@ubuntu-jmeter:/home/mycisco# openssl s_client -connect www.salesforce.com:443 -tls1 -showcerts CONNECTED(00000003) depth=1 C = US, ST = F5, L = F5, O = F5, OU = F5, CN = *.*.com verify error:num=19:self signed certificate in certificate chain verify return:0 --- Certificate chain 0 s:/C=US/ST=California/L=San Francisco/O=Salesforce.com, Inc./OU=Network/CN=www.salesforce.com i:/C=US/ST=F5/L=F5/O=F5/OU=F5/CN=*.*.com -----BEGIN CERTIFICATE----- MIIESDCCAzCgAwIBAgIIVdRE42Zx7NMwDQYJKoZIhvcNAQELBQAwUzELMAkGA1UE BhMCVVMxCzAJBgNVBAgTAkY1MQswCQYDVQQHEwJGNTELMAkGA1UEChMCRjUxCzAJ BgNVBAsTAkY1MRAwDgYDVQQDFAcqLiouY29tMB4XDTE1MDgxODA4NTcwN1oXDTE1 MDkxODA4NTcwN1owgYgxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpDYWxpZm9ybmlh MRYwFAYDVQQHFA1TYW4gRnJhbmNpc2NvMR0wGwYDVQQKFBRTYWxlc2ZvcmNlLmNv bSwgSW5jLjEQMA4GA1UECxQHTmV0d29yazEbMBkGA1UEAxQSd3d3LnNhbGVzZm9y Y2UuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAxQP5IrzYicGd cVDYp1nplorSElQfGBkE8I+9TLmD6iCxl7gKdqVYaF9FQujyhmSUitHR52YRyCha CjnJ2/wpzyiew/Ny3azXRRfEZTMPhYArruSNhGd8u1KRUfFWG2BPjWQgq5NVOxRH XJKiZ+3WGd1KlSqpVT9iY+qCThMw92HLH3eZdfGbskr7qqTOu6O8Hgy01IGVpg4l 6VtbJwOosRFIiRRemvRXWPX8X3fOVoc5GmYsuP1UtQCzpHkc3yXk51S9xmIZ41C1 cywoUZUNNQXF+hWFM1pDz1s7LjW8h5rcdx6UN5QixhIs8SRPc8hhDIRPPyIfDG4f id1dIEhGgQIDAQABo4HpMIHmMIHYBgNVHREEgdAwgc2CEnd3dy5zYWxlc2ZvcmNl LmNvbYIOc2FsZXNmb3JjZS5jb22CDnNmZGNzdGF0aWMuY29tggtjaGF0dGVyLmNv bYIJZm9yY2UuY29tgghkYXRhLmNvbYIQKi5zZmRjc3RhdGljLmNvbYINKi5jaGF0 dGVyLmNvbYILKi5mb3JjZS5jb22CCiouZGF0YS5jb22CCCouZG8uY29tggZkby5j b22CEGMuc2FsZXNmb3JjZS5jb22CF29yaWdpbi1jLnNhbGVzZm9yY2UuY29tMAkG A1UdEwQCMAAwDQYJKoZIhvcNAQELBQADggEBAB3xkIDZKfDST+sXIdeOd1spl0vP iGBUhpRx6l8HC7X3KohX4EwEm+ls4gY/dcpudc1hRB/Sh438KcwogHRWrPchiFVm bKAXlVeW1aUmhya3Zqooi+qaA/TEe0r861k339ZGnwyqtpqSd9GnbSwvGyukTVcM NzyRfYzBRzeGWOTYEJrrUhzxEF7pwjrokYPbKk5lyiuKOfMcD5UFDxK3qtr5+96h /+fKObwRGtpnwiJd4kpXv6vvd12LbU/EdkPD2gNO1PSeq+NiyZhb/uTCFai6S+19 bHl3ZaaLQJToLLiuWrmnmiMxKU33WD+JK8q9bGX4cLLiSZiTwGiYW7zVlFA= -----END CERTIFICATE----- 1 s:/C=US/ST=F5/L=F5/O=F5/OU=F5/CN=*.*.com i:/C=US/ST=F5/L=F5/O=F5/OU=F5/CN=*.*.com -----BEGIN CERTIFICATE----- MIIDIjCCAgqgAwIBAgIECpaE6zANBgkqhkiG9w0BAQsFADBTMQswCQYDVQQGEwJV UzELMAkGA1UECBMCRjUxCzAJBgNVBAcTAkY1MQswCQYDVQQKEwJGNTELMAkGA1UE CxMCRjUxEDAOBgNVBAMUByouKi5jb20wHhcNMTUwODE5MDcyOTQ3WhcNMTYwODE4 MDcyOTQ3WjBTMQswCQYDVQQGEwJVUzELMAkGA1UECBMCRjUxCzAJBgNVBAcTAkY1 MQswCQYDVQQKEwJGNTELMAkGA1UECxMCRjUxEDAOBgNVBAMUByouKi5jb20wggEi MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDVjXf8woBn8Nl1AGc07qTkwiel p3d31tTDRBGi0hXBnMni9xGf3K58uITnrunpJvUctM1UYiENzbuiTbK6CN43sDfZ YxXDNmEpOExX1AsOala8Luatl+NVLMLBkQIjjKXwiOn+fGhbwqN9Puh2pTRnet32 AZ9D9U+G4tytDgqLwR4EXlPNXMa1Hicv9Y4hQUULaCdgez5szSWvCsk2/SA6NLsC tiu1aTT30o52CBFK3L/KCtf3b0S98bS/ZKu5Pp4eryZnmqOrtAMRL2iXIIKDKsu5 uPg7aG9OT78t9LN+Jd10UXzF8/WPhpK+iY122JwHrKlg2tPRtXXeybkb33DhAgMB AAEwDQYJKoZIhvcNAQELBQADggEBAFgYuj9PcRu24YaqJ4O46w/fK7jflSxsNAvn 8eX+5stXaTY4zq4m1iUBMwpE0qzaV+2wAG8B9bHoANwqyKjdctKcUjc35rco01/S qYtBUT54k4HeIQMozu3NF2Zhu41bLAO6lzOQd6z+N2Ysp+nwTYVL8IpJNaNWkjZb fSa6BXGTW9PqAccoSdx4M+aLX2YkXEovJt5McEkwKr7iTFOwmVZjMbNWXrrCg2Yc drzeClIqbYf8zmsZZLJUMeD2Lrst8zfr62OnWGkCl+V8i51fBNxdp4EZxE0z5UzC kbvmQDF+ja+tim7/Fr5pGAwwEgkk9zkJbcJovwcM6zdl/SwzbJ0= -----END CERTIFICATE----- --- Server certificate subject=/C=US/ST=California/L=San Francisco/O=Salesforce.com, Inc./OU=Network/CN=www.salesforce.com issuer=/C=US/ST=F5/L=F5/O=F5/OU=F5/CN=*.*.com --- No client certificate CA names sent --- SSL handshake has read 2608 bytes and written 401 bytes --- New, TLSv1/SSLv3, Cipher is DHE-RSA-AES256-SHA Server public key is 2048 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE SSL-Session: Protocol : TLSv1 Cipher : DHE-RSA-AES256-SHA Session-ID: 5906A738CBFC57B07ACBE0BDB30C51740053406E4090642EB68FF106BEE40418 Session-ID-ctx: Master-Key: 6900D98D17C3784970CE7943B8429566415DAE2915D1E3DC0192356DF602AE7126361A6C3B2585166972B9A057E871D8 Key-Arg : None PSK identity: None PSK identity hint: None SRP username: None Start Time: 1439974625 Timeout : 7200 (sec) Verify return code: 19 (self signed certificate in certificate chain) --- |
注意看上述最后的证书是F5自己签发的:
|
1 2 3 |
Server certificate subject=/C=US/ST=California/L=San Francisco/O=Salesforce.com, Inc./OU=Network/CN=www.salesforce.com issuer=/C=US/ST=F5/L=F5/O=F5/OU=F5/CN=*.*.com |
2. Bypass情形,即客户端看到实际真实server证书
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 |
root@ubuntu-jmeter:/home/mycisco# openssl s_client -connect devcentral.f5.com:443 -tls1 -showcerts CONNECTED(00000003) depth=2 C = US, O = "Entrust, Inc.", OU = See www.entrust.net/legal-terms, OU = "(c) 2009 Entrust, Inc. - for authorized use only", CN = Entrust Root Certification Authority - G2 verify error:num=20:unable to get local issuer certificate verify return:0 --- Certificate chain 0 s:/C=US/ST=Washington/L=Seattle/1.3.6.1.4.1.311.60.2.1.3=US/1.3.6.1.4.1.311.60.2.1.2=Washington/O=F5 Networks Inc/businessCategory=Private Organization/serialNumber=601692492/CN=f5.com i:/C=US/O=Entrust, Inc./OU=See www.entrust.net/legal-terms/OU=(c) 2014 Entrust, Inc. - for authorized use only/CN=Entrust Certification Authority - L1M -----BEGIN CERTIFICATE----- MIIHYzCCBkugAwIBAgIEVMwsYzANBgkqhkiG9w0BAQsFADCBujELMAkGA1UEBhMC VVMxFjAUBgNVBAoTDUVudHJ1c3QsIEluYy4xKDAmBgNVBAsTH1NlZSB3d3cuZW50 cnVzdC5uZXQvbGVnYWwtdGVybXMxOTA3BgNVBAsTMChjKSAyMDE0IEVudHJ1c3Qs IEluYy4gLSBmb3IgYXV0aG9yaXplZCB1c2Ugb25seTEuMCwGA1UEAxMlRW50cnVz dCBDZXJ0aWZpY2F0aW9uIEF1dGhvcml0eSAtIEwxTTAeFw0xNTA3MjcxNjM5MzJa Fw0xNjA3MjgwNjMzNDlaMIHEMQswCQYDVQQGEwJVUzETMBEGA1UECBMKV2FzaGlu Z3RvbjEQMA4GA1UEBxMHU2VhdHRsZTETMBEGCysGAQQBgjc8AgEDEwJVUzEbMBkG CysGAQQBgjc8AgECEwpXYXNoaW5ndG9uMRgwFgYDVQQKEw9GNSBOZXR3b3JrcyBJ bmMxHTAbBgNVBA8TFFByaXZhdGUgT3JnYW5pemF0aW9uMRIwEAYDVQQFEwk2MDE2 OTI0OTIxDzANBgNVBAMTBmY1LmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC AQoCggEBANoelpLBCHNTmx0/tUPMHr9k6VCHXk97GRbmcOFJrhWm2Y5pRzKniiIr gQwOvI/Ntcjlqyzdj5rvL8PD5+Wwe1akV4h2bCdFjg0G6THtNFNywkwJX93H0hWD iLaiUXfwdliXvSZu4DavDGdYkrSHBNE4FNY0nU0kgb7C6Ps+jhXrvJMUiS0a1s1t fU//7uwc4v5aM6/XY7JWHRTnqo4kYvMqGPbSogsDcrzNRTtzAY7L7Jj4rJJnX1zD uyw05FabtBQRY4fIMPAl+KTiFiQaiLINk4m8gjSmuIrr/QEzVFpFHxYovcl+7Wnx 4Fxl9B37XpBtkXzU5QHcRz3fGmVK91MCAwEAAaOCA2MwggNfMIGBBgNVHREEejB4 ggZmNS5jb22CCnd3dy5mNS5jb22CEWRldmNlbnRyYWwuZjUuY29tgg9saW5lcmF0 ZS5mNS5jb22CEHN5bnRoZXNpcy5mNS5jb22CDnBhcnRuZXIuZjUuY29tgg9wYXJ0 bmVycy5mNS5jb22CC2RvY3MuZjUuY29tMIIBfgYKKwYBBAHWeQIEAgSCAW4EggFq AWgAdgBo9pj4H2SCvjqM7rkoHUz8cVFdZ5PURNEKZ6y7T0/7xAAAAU7QfZObAAAE AwBHMEUCIQDUOjKBA7cIHCMfX7RZg2rhKYc3QfmlkRdBvQPimByb7QIgLZgNUi60 1CT3r/sFzn1U9ZCbiHRnn4ULjLB3RjBkKTkAdgBWFAaaL9fC7NP14b1Esj7HRna5 vJkRXMDvlJhV1onQ3QAAAU7QfZdJAAAEAwBHMEUCIBL043XtG7YgNNtmxKuqDfuS xTa7+kDE4IoS1DIW51hvAiEAkrH+eSesmozeik6LSHnT8gZ2rfqPxnYO/m1ah++w kloAdgB0YbSgnPs9QddRWVdbLnZJpEWo0ncJsMxWSmSCt+tBowAAAU7QfZnJAAAE AwBHMEUCICUKH09E8D3uTAPUDaSHuRKkqPJL4YQuhOLORUJ/gRMpAiEAi3BE/PEn b9McJHNsvqlgR+HKECM0TvASBSo8RGYwqnMwCwYDVR0PBAQDAgWgMB0GA1UdJQQW MBQGCCsGAQUFBwMBBggrBgEFBQcDAjBoBggrBgEFBQcBAQRcMFowIwYIKwYBBQUH MAGGF2h0dHA6Ly9vY3NwLmVudHJ1c3QubmV0MDMGCCsGAQUFBzAChidodHRwOi8v YWlhLmVudHJ1c3QubmV0L2wxbS1jaGFpbjI1Ni5jZXIwMwYDVR0fBCwwKjAooCag JIYiaHR0cDovL2NybC5lbnRydXN0Lm5ldC9sZXZlbDFtLmNybDBBBgNVHSAEOjA4 MDYGCmCGSAGG+mwKAQIwKDAmBggrBgEFBQcCARYaaHR0cDovL3d3dy5lbnRydXN0 Lm5ldC9ycGEwHwYDVR0jBBgwFoAUw/fQtSowra8NkSFwOVTdvIlwxzowHQYDVR0O BBYEFNGOaMCt0oswqTyiCr0xrG/5/q5gMAkGA1UdEwQCMAAwDQYJKoZIhvcNAQEL BQADggEBAA2Fq+f6rP4H2DQhXiWxohbMNikb5BjcP6pDs5guSLTMp3G1DO/WoSEw WFeHQEYH77TPEJ9komc8Y+9T9ypLHb0/aLIh6VfZSLV9+Wqnsc/pw46izkw1rIcc Jjl57OshV3zvyEb8+Uf6Mz2kmq4yKpNfiBRspKfh4smsaY53pYx3TcSbrv9Kepzc rUFFK67Xk63VXdFPYGCoXgZK/nvYG7XYXrgWc+y5s6yTEiEos38OAVIG80iQEFB3 ZZ/bn78prX1z+r2JjjvajAk9zkv3CrnIGZPXGbD5GOTAczC712gnq1aVs0e0n+Sk gTTZMbcQsUzLutNb0e3+R0N9aaad5cQ= -----END CERTIFICATE----- 1 s:/C=US/O=Entrust, Inc./OU=See www.entrust.net/legal-terms/OU=(c) 2014 Entrust, Inc. - for authorized use only/CN=Entrust Certification Authority - L1M i:/C=US/O=Entrust, Inc./OU=See www.entrust.net/legal-terms/OU=(c) 2009 Entrust, Inc. - for authorized use only/CN=Entrust Root Certification Authority - G2 -----BEGIN CERTIFICATE----- MIIFLTCCBBWgAwIBAgIMYaHn0gAAAABR02amMA0GCSqGSIb3DQEBCwUAMIG+MQsw CQYDVQQGEwJVUzEWMBQGA1UEChMNRW50cnVzdCwgSW5jLjEoMCYGA1UECxMfU2Vl IHd3dy5lbnRydXN0Lm5ldC9sZWdhbC10ZXJtczE5MDcGA1UECxMwKGMpIDIwMDkg RW50cnVzdCwgSW5jLiAtIGZvciBhdXRob3JpemVkIHVzZSBvbmx5MTIwMAYDVQQD EylFbnRydXN0IFJvb3QgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkgLSBHMjAeFw0x NDEyMTUxNTI1MDNaFw0zMDEwMTUxNTU1MDNaMIG6MQswCQYDVQQGEwJVUzEWMBQG A1UEChMNRW50cnVzdCwgSW5jLjEoMCYGA1UECxMfU2VlIHd3dy5lbnRydXN0Lm5l dC9sZWdhbC10ZXJtczE5MDcGA1UECxMwKGMpIDIwMTQgRW50cnVzdCwgSW5jLiAt IGZvciBhdXRob3JpemVkIHVzZSBvbmx5MS4wLAYDVQQDEyVFbnRydXN0IENlcnRp ZmljYXRpb24gQXV0aG9yaXR5IC0gTDFNMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A MIIBCgKCAQEA0IHBOSPCsdHs91fdVSQ2kSAiSPf8ylIKsKs/M7WwhAf23056sPuY Ij0BrFb7cW2y7rmgD1J3q5iTvjOK64dex6qwymmPQwhqPyK/MzlG1ZTy4kwFItln gJHxBEoOm3yiydJs/TwJhL39axSagR3nioPvYRZ1R5gTOw2QFpi/iuInMlOZmcP7 lhw192LtjL1JcdJDQ6Gh4yEqI3CodT2ybEYGYW8YZ+QpfrI8wcVfCR5uRE7sIZlY FUj0VUgqtzS0BeN8SYwAWN46lsw53GEzVc4qLj/RmWLoquY0djGqr3kplnjLgRSv adr7BLlZg0SqCU+01CwBnZuUMWstoc/B5QIDAQABo4IBKzCCAScwDgYDVR0PAQH/ BAQDAgEGMB0GA1UdJQQWMBQGCCsGAQUFBwMCBggrBgEFBQcDATASBgNVHRMBAf8E CDAGAQH/AgEAMDMGCCsGAQUFBwEBBCcwJTAjBggrBgEFBQcwAYYXaHR0cDovL29j c3AuZW50cnVzdC5uZXQwMAYDVR0fBCkwJzAloCOgIYYfaHR0cDovL2NybC5lbnRy dXN0Lm5ldC9nMmNhLmNybDA7BgNVHSAENDAyMDAGBFUdIAAwKDAmBggrBgEFBQcC ARYaaHR0cDovL3d3dy5lbnRydXN0Lm5ldC9ycGEwHQYDVR0OBBYEFMP30LUqMK2v DZEhcDlU3byJcMc6MB8GA1UdIwQYMBaAFGpyJnrQHu995ztpUdRsjZ+QEmarMA0G CSqGSIb3DQEBCwUAA4IBAQC0h8eEIhopwKR47PVPG7SEl2937tTPWa+oQ5YvHVje pvMVWy7ZQ5xMQrkXFxGttLFBx2YMIoYFp7Qi+8VoaIqIMthx1hGOjlJ+Qgld2dnA DizvRGsf2yS89byxqsGK5Wbb0CTz34mmi/5e0FC6m3UAyQhKS3Q/WFOv9rihbISY Jnz8/DVRZZgeO2x28JkPxLkJ1YXYJKd/KsLak0tkuHB8VCnTglTVz6WUwzOeTTRn 4Dh2ZgCN0C/GqwmqcvrOLzWJ/MDtBgO334wlV/H77yiI2YIowAQPlIFpI+CRKMVe 1QzX1CA778n4wI+nQc1XRG5sZ2L+hN/nYNjvv9QiHg3n -----END CERTIFICATE----- 2 s:/C=US/O=Entrust, Inc./OU=See www.entrust.net/legal-terms/OU=(c) 2009 Entrust, Inc. - for authorized use only/CN=Entrust Root Certification Authority - G2 i:/C=US/O=Entrust, Inc./OU=www.entrust.net/CPS is incorporated by reference/OU=(c) 2006 Entrust, Inc./CN=Entrust Root Certification Authority -----BEGIN CERTIFICATE----- MIIE/zCCA+egAwIBAgIEUdNARDANBgkqhkiG9w0BAQsFADCBsDELMAkGA1UEBhMC VVMxFjAUBgNVBAoTDUVudHJ1c3QsIEluYy4xOTA3BgNVBAsTMHd3dy5lbnRydXN0 Lm5ldC9DUFMgaXMgaW5jb3Jwb3JhdGVkIGJ5IHJlZmVyZW5jZTEfMB0GA1UECxMW KGMpIDIwMDYgRW50cnVzdCwgSW5jLjEtMCsGA1UEAxMkRW50cnVzdCBSb290IENl cnRpZmljYXRpb24gQXV0aG9yaXR5MB4XDTE0MDkyMjE3MTQ1N1oXDTI0MDkyMzAx MzE1M1owgb4xCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1FbnRydXN0LCBJbmMuMSgw JgYDVQQLEx9TZWUgd3d3LmVudHJ1c3QubmV0L2xlZ2FsLXRlcm1zMTkwNwYDVQQL EzAoYykgMjAwOSBFbnRydXN0LCBJbmMuIC0gZm9yIGF1dGhvcml6ZWQgdXNlIG9u bHkxMjAwBgNVBAMTKUVudHJ1c3QgUm9vdCBDZXJ0aWZpY2F0aW9uIEF1dGhvcml0 eSAtIEcyMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAuoS2ctueDGvi mekwAad26jK4lUEaydphTlhyz/72gnm/c2EGCqUn2LNf00VOHHLWTjLycooP94MZ 0GqAgABFHrDH55q/ElcnHKNoLwqHvWprDl5l8xx31dSFjXAhtLMy54ui1YY5ArG4 0kfO5MlJxDun3vtUfVe+8OhuwnmyOgtV4lCYFjITXC94VsHClLPyWuQnmp8k18bs 0JslguPMwsRFxYyXegZrKhGfqQpuSDtv29QRGUL3jwe/9VNfnD70FyzmaaxOMkxi d+q36OW7NLwZi66cUee3frVTsTMi5W3PcDwa+uKbZ7aD9I2lr2JMTeBYrGQ0EgP4 to2UYySkcQIDAQABo4IBDzCCAQswDgYDVR0PAQH/BAQDAgEGMBIGA1UdEwEB/wQI MAYBAf8CAQEwMwYIKwYBBQUHAQEEJzAlMCMGCCsGAQUFBzABhhdodHRwOi8vb2Nz cC5lbnRydXN0Lm5ldDAzBgNVHR8ELDAqMCigJqAkhiJodHRwOi8vY3JsLmVudHJ1 c3QubmV0L3Jvb3RjYTEuY3JsMDsGA1UdIAQ0MDIwMAYEVR0gADAoMCYGCCsGAQUF BwIBFhpodHRwOi8vd3d3LmVudHJ1c3QubmV0L0NQUzAdBgNVHQ4EFgQUanImetAe 733nO2lR1GyNn5ASZqswHwYDVR0jBBgwFoAUaJDkZ6SmU4DHhmak8fdLQ/uEvW0w DQYJKoZIhvcNAQELBQADggEBAGkzg/woem99751V68U+ep11s8zDODbZNKIoaBjq HmnTvefQd9q4AINOSs9v0fHBIj905PeYSZ6btp7h25h3LVY0sag82f3Azce/BQPU AsXx5cbaCKUTx2IjEdFhMB1ghEXveajGJpOkt800uGnFE/aRs8lFc3a2kvZ2Clvh A0e36SlMkTIjN0qcNdh4/R0f5IOJJICtt/nP5F2l1HHEhVtwH9s/HAHrGkUmMRTM Zb9n3srMM2XlQZHXN75BGpad5oqXnafOrE6aPb0BoGrZTyIAi0TVaWJ7LuvMuueS fWlnPfy4fN5Bh9Bp6roKGHoalUOzeXEodm2h+1dK7E3IDhA= -----END CERTIFICATE----- --- Server certificate subject=/C=US/ST=Washington/L=Seattle/1.3.6.1.4.1.311.60.2.1.3=US/1.3.6.1.4.1.311.60.2.1.2=Washington/O=F5 Networks Inc/businessCategory=Private Organization/serialNumber=601692492/CN=f5.com issuer=/C=US/O=Entrust, Inc./OU=See www.entrust.net/legal-terms/OU=(c) 2014 Entrust, Inc. - for authorized use only/CN=Entrust Certification Authority - L1M --- No client certificate CA names sent --- SSL handshake has read 5024 bytes and written 337 bytes --- New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-SHA Server public key is 2048 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE SSL-Session: Protocol : TLSv1 Cipher : ECDHE-RSA-AES256-SHA Session-ID: A8760111EB8C0DF23198F6AEC9F4E0A42D96DC6B05D07E45780B522884C51209 Session-ID-ctx: Master-Key: BBEA7D60B20CE20FE995F36D40B4DB5686F749BB494B1633858CC6604EB4D17DEB87A8DEFA97E5AAA28411D1311C5414 Key-Arg : None PSK identity: None PSK identity hint: None SRP username: None Start Time: 1439974518 Timeout : 7200 (sec) Verify return code: 20 (unable to get local issuer certificate) --- |
注意看证书是是未经过F5签发的而是原始的entrust签发的证书
|
1 2 3 |
Server certificate subject=/C=US/ST=Washington/L=Seattle/1.3.6.1.4.1.311.60.2.1.3=US/1.3.6.1.4.1.311.60.2.1.2=Washington/O=F5 Networks Inc/businessCategory=Private Organization/serialNumber=601692492/CN=f5.com issuer=/C=US/O=Entrust, Inc./OU=See www.entrust.net/legal-terms/OU=(c) 2014 Entrust, Inc. - for authorized use only/CN=Entrust Certification Authority - L1M |
其他问题:
-
这个功能需要license,非免费
-
该功能不支持server要求双向验证的情形,对于这种情况默认是无法进行处理的,因为在通信过程中的第3步会失败,进而导致F5 reset client侧连接。
Bugs:
sol16360: The SSL Forward Proxy feature does not fully support the SSL Forward Proxy Bypass option
sol15830: Changes made to a data group are not automatically propagated to a Client SSL profile
另外,上述假定访问vs的都是标准的HTTPS请求,实际应用很可能是一个全0的通配类VS,那么此时需要考虑一些irule,利用irule判断如果是一个SSL握手,则启用ssl profle功能,否则关闭SSL profile,类似这样
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
when CLIENT_ACCEPTED { # Assume it is not ssl HTTP::disable SSL::disable clientside SSL::disable serverside TCP::collect } when CLIENT_DATA { # Enable SSL,if it is client hello packet. binary scan [TCP::payload] c type if { $type == 22 } { SSL::enable clientside SSL::enable serverside HTTP::enable } TCP::release } |
附加信息,在一个全0的通配端口的vs上,当一个tls1.0以上版本的ssl 请求的话,识别其SNI是否在2way——ssl的bypass group中,如果匹配则vs当成普通转发vs,如果不匹配则启用两侧ssl profile进行SSL forward处理。并针对一些匹配条件启动SSL forward bypass策略。 对于SSLV3,由于不适用于ssl forward功能,直接当成普通vs转发。注意下述irule对没有提供SNI且服务器要求2way-ssl的情形是无法处理的。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 |
when CLIENT_ACCEPTED { # On TCP session initiation, we dont know if this is going to be SSL # disable SSL and HTTP profiles and then collect the payload set detect_handshake 1 HTTP::disable SSL::disable clientside SSL::disable serverside TCP::collect } when CLIENT_DATA { # If we're in a handshake detection, look for an SSL/TLS header. binary scan [TCP::payload] cSS tls_xacttype tls_version tls_recordlen log local0. "ssl version $tls_version" # TLS is the only thing we want to process because it's the only # version that allows the servername extension to be present. When we # find a supported TLS version, we'll check to make sure we're getting # only a Client Hello transaction -- those are the only ones we can pull # the servername from prior to connection establishment. switch $tls_version { "768" { set detect_handshake 0 } "769" - "770" - "771" { if { ($tls_xacttype == 22) } { binary scan [TCP::payload] @5c tls_action if { not (($tls_action == 1) && ([TCP::payload length] > $tls_recordlen)) } { set detect_handshake 0 } } } default { log local0. "it is not ssl handshake packet!" set detect_handshake 0 } } if { ($detect_handshake) } { log local0. "Found ssl handshake" # If we made it this far, we're still processing a TLS client hello. # # Skip the TLS header (43 bytes in) and process the record body. For TLS/1.0 we # expect this to contain only the session ID, cipher list, and compression # list. All but the cipher list will be null since we're handling a new transaction # (client hello) here. We have to determine how far out to parse the initial record # so we can find the TLS extensions if they exist. set record_offset 43 binary scan [TCP::payload] @${record_offset}c tls_sessidlen set record_offset [expr {$record_offset + 1 + $tls_sessidlen}] binary scan [TCP::payload] @${record_offset}S tls_ciphlen set record_offset [expr {$record_offset + 2 + $tls_ciphlen}] binary scan [TCP::payload] @${record_offset}c tls_complen set record_offset [expr {$record_offset + 1 + $tls_complen}] # If we're in TLS and we've not parsed all the payload in the record # at this point, then we have TLS extensions to process. We will detect # the TLS extension package and parse each record individually. if { ([TCP::payload length] > $record_offset) } { binary scan [TCP::payload] @${record_offset}S tls_extenlen set record_offset [expr {$record_offset + 2}] binary scan [TCP::payload] @${record_offset}a* tls_extensions # Loop through the TLS extension data looking for a type 00 extension # record. This is the IANA code for server_name in the TLS transaction. for { set x 0 } { $x < $tls_extenlen } { incr x 4 } { set start [expr {$x}] binary scan $tls_extensions @${start}SS etype elen if { ($etype == "00") } { # A servername record is present. Pull this value out of the packet data # and save it for later use. We start 9 bytes into the record to bypass # type, length, and SNI encoding header (which is itself 5 bytes long), and # capture the servername text (minus the header). set grabstart [expr {$start + 9}] set grabend [expr {$elen - 5}] binary scan $tls_extensions @${grabstart}A${grabend} tls_servername log local0. "SNI name is $tls_servername" set start [expr {$start + $elen}] } else { # Bypass all other TLS extensions. set start [expr {$start + $elen}] } set x $start } # Check to see whether we got a servername indication from TLS. If so, # make the appropriate changes. if { ([info exists tls_servername] ) } { # For sites in the bypass_group, we will disable all sides ssl, for not in the group, will enable ssl. if { not [class match $tls_servername contains bypass_2way_host] } { SSL::enable clientside SSL::enable serverside HTTP::enable } } else { # SNI does not exisit log local0. "It is ssl handshake,but SNI not exist,enable ssl for both side" SSL::enable clientside SSL::enable serverside HTTP::enable } set detect_handshake 0 } } TCP::release } when CLIENTSSL_CLIENTHELLO { # Extract SNI header from client if { [SSL::extensions exists -type 0] } { binary scan [SSL::extensions -type 0] @9a* ssl_ext_sn #set category 0 #catch { set category [getfield [CATEGORY::lookup http://$ssl_ext_sn/] " " 1] } #log local0.alert "SSL SNI $ssl_ext_sn category=$category ([IP::client_addr]:[TCP::client_port] --> [IP::local_addr]:[TCP::local_port])" } } when CLIENTSSL_SERVERHELLO_SEND { # Bypass ssl forward proxy based destination port if { [ class match [TCP::local_port] equals bypass_port ] } { #log local0.alert "*** Bypass SSL for dst port [IP::client_addr]:[TCP::client_port] --> [IP::local_addr]:[TCP::local_port]" SSL::forward_proxy policy bypass HTTP::disable } # Bypass ssl forward proxy based destination IP if { [ class match [IP::local_addr] equals bypass_address ] } { #log local0.alert "*** Bypass SSL for IP [IP::client_addr]:[TCP::client_port] --> [IP::local_addr]:[TCP::local_port]" SSL::forward_proxy policy bypass HTTP::disable } # Bypass ssl forward proxy based on SNI hostname if { [info exists ssl_ext_sn] && [ class match $ssl_ext_sn contains bypass_host ] } { log local0.alert "*** Bypass SSL for HOST $ssl_ext_sn ([IP::client_addr]:[TCP::client_port] --> [IP::local_addr]:[TCP::local_port])" SSL::forward_proxy policy bypass HTTP::disable } # Bypass ssl forward proxy based on category #if { [info exists ssl_ext_sn] && [ class match $category equals bypass_category ] } { #log local0.alert "*** Bypass SSL for $category $ssl_ext_sn ([IP::client_addr]:[TCP::client_port] --> [IP::local_addr]:[TCP::local_port])" #SSL::forward_proxy policy bypass #HTTP::disable #} } when HTTP_REQUEST { # Insert header in request to for re-encryption when request is returned from inspection proxy to BIG-IP #log local0.alert "[virtual] insert X-Proxy-HTTPS http://[HTTP::host]/[string range [HTTP::uri] 1 25]..." # HTTP::header insert X-Proxy-HTTPS [TCP::local_port] #LB::detach #SSL::disable serverside #virtual vs-any-proxy2 log local0. "http request event" } |

文章评论