今天恢复防火墙,突然对一个问题疑惑了,于是赶紧看书,原来我在书上竟然赫然有着我以前的标记,怎么还是会模糊呢?
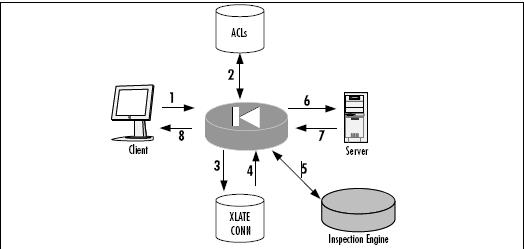
1. The client generates a SYN packet, headed toward the server, to
establish a new connection.
2. The PIX investigates the ACL to determine if the information flow
control policy should permit the new connection.
3. Assuming the connection is valid, the PIX updates the connections table.
4. The XLATE table is updated as necessary.
5. The stream is processed by the Application Inspection Engine, if
necessary, which could involve rewriting the packet.
6. The packet is sent on to the server.
7. On the reverse path, the server responds with its SYN/ACK.
8. However, since this is not an initialization request, inspection of the rule
base is not required; it looks the packet up in the connections table and
then forwards it back to the client.

文章评论