How DNSSEC works
Like other Internet services, DNS (DNS – Domain Name System) was created in times when only a small number of nodes were connected to the Internet and operators of these nodes knew each other. As the numbers of people and computers connected grew later, it was necessary to start dealing with security of the services. All those Internet users no longer know one another and sadly not all of them connect to the network with good intentions.
DNSSEC is an extension to the DNS system, increasing the domain name service security. The principle of DNS is the translation of name-based Internet addresses such as www.nic.cz or www.nicedomain.cz to numeric addresses that can be understood by computers and used to display specific web pages, send e-mail, make phone calls over the Internet and provide other common Internet services. DNSSEC enhances the security when using DNS by preventing insertion of fake, altered or incomplete domain name data.
The DNS service provides potential attackers several spots where the communication can be disrupted and fake data inserted while not secured by DNSSEC. By altering the domain name data, the attacker modifies behavior of other Internet services which can be misused in this way. Attackers can achieve the following effects, for example:
- Read other people's e-mail
- Use fake websites to obtain passwords, access codes or payment card data etc. (known as phishing)
- Bypass anti-spam protection in DNS and spread spam
- Counterfeit messages and information displayed on websites
- Redirect or wiretap on phone calls routed through Internet
Users have mostly no chance to recognize that something wrong is happening. However, deployment of DNSSEC lets users rest reassured that the information they obtain from DNS came from the correct source, was complete and its integrity was not compromised during the transfer. DNSSEC ensures that the DNS data can be trusted.
How Does DNSSEC Work?
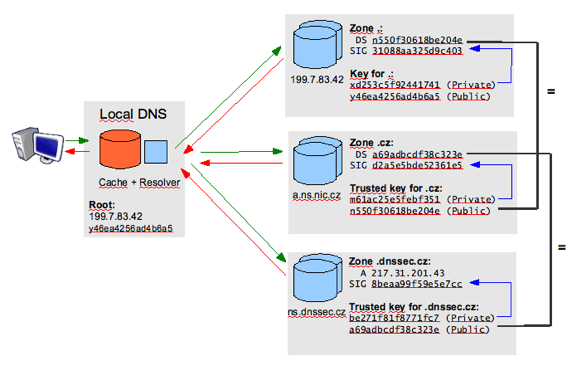
DNSSEC introduces asymmetric cryptography to DNS – i.e. one key is used for content encryption while a different key allows to decrypt the content. A similar principle forms the basis of the more widely known encryption of e-mail messages using PGP or signing of messages using electronic signatures. In the case of DNSSEC a domain user generates a pair of keys – private key and public key. The user then electronically signs all technical data he/she is entering to DNS for the given domain with the private key. The public key allows to verify the validity of such signature. To provide access to the public key for all other users, the key is published for the domain at the superior authority. For all .CZ domains the keys are published in the .CZ domain registry. The technical data in DNS are signed even on the .CZ domain registry level while the public key for this signature is handed over to the superior authority by the registry administrator. This creates a chain of trust ensuring that we can rely on the data as long as all links of the chain remain intact and all electronic signatures match. See the following scheme.
What Will Change When DNSSEC Is Implemented?
DNSSEC provides backward compatibility with the existing DNS, meaning that both version work simultaneously. It is therefore likely that common users will face no changes at all when DNSSEC is implemented for .CZ domains. This will be true until users start using DNSSEC on a specific DNS server. This can apply directly to users' computers in the case of experts, to company servers in the case of companies or to ISP servers in the case of home users. Service and content providers can take advantage of DNSSEC to increase the security and trustworthiness of their services. Once DNSSEC is in place, the providers will need to enable and maintain digital signatures of their data in DNS as well as publish respective encryption keys in the .CZ domains registry.
相关网站
http://www.root-dnssec.org/
https://www.iana.org/dnssec/

文章评论