拉取busybox镜像,并运行一个容器实例(挂载一个自命名的volume进去)
|
1 |
[root@docker1 volumes]# docker run -it -v /root/dockervolume/:/data busybox |
观察此时/var/lib/docker下结构:
[root@docker1 docker]# tree -L 4
.
├── containers
│ ├── 276041ef9cbefee243480ed52e5d2e0529df7a7c6c6a617f38ab6937136079f3
│ │ ├── 276041ef9cbefee243480ed52e5d2e0529df7a7c6c6a617f38ab6937136079f3-json.log
│ │ ├── checkpoints
│ │ ├── config.v2.json
│ │ ├── hostconfig.json
│ │ ├── hostname
│ │ ├── hosts
│ │ ├── resolv.conf
│ │ ├── resolv.conf.hash
│ │ └── shm
│ └── 985e538f6b25487f5944707d44db1c3f624dd83f95adf02ab901fc75e6750823
│ ├── 985e538f6b25487f5944707d44db1c3f624dd83f95adf02ab901fc75e6750823-json.log
│ ├── checkpoints
│ ├── config.v2.json
│ ├── hostconfig.json
│ ├── hostname
│ ├── hosts
│ ├── resolv.conf
│ ├── resolv.conf.hash
│ └── shm
├── image
│ └── overlay
│ ├── distribution
│ │ ├── diffid-by-digest
│ │ └── v2metadata-by-diffid
│ ├── imagedb
│ │ ├── content
│ │ └── metadata
│ ├── layerdb
│ │ ├── mounts
│ │ ├── sha256
│ │ └── tmp
│ └── repositories.json
├── network
│ └── files
│ └── local-kv.db
├── overlay
│ ├── 14d4a3283bd0fac4850cf1151a5699266e62ac0366e15d6a290fe13ab6a452cd
│ │ ├── lower-id
│ │ ├── merged
│ │ ├── upper
│ │ │ ├── dev
│ │ │ ├── etc
│ │ │ ├── proc
│ │ │ └── sys
│ │ └── work
│ │ └── work
│ ├── 14d4a3283bd0fac4850cf1151a5699266e62ac0366e15d6a290fe13ab6a452cd-init
│ │ ├── lower-id
│ │ ├── merged
│ │ ├── upper
│ │ │ ├── dev
│ │ │ ├── etc
│ │ │ ├── proc
│ │ │ └── sys
│ │ └── work
│ │ └── work
│ ├── 4ff8b86a0317b5a6bd539e51ec676395e6079f4d8a77b34ff95cb8a9451279a0
│ │ └── root
│ │ └── hello
│ ├── a626a89bd36ab93ba340eb98f01a824b1edb75082694cc8c695992b4e57e1087
│ │ └── root
│ │ ├── bin
│ │ ├── dev
│ │ ├── etc
│ │ ├── home
│ │ ├── root
│ │ ├── tmp
│ │ ├── usr
│ │ └── var
│ ├── c1eb6f4be0f4f384fe4a1645cc03e3f9c3c81c72a9f276c844f62c6d7cca0974
│ │ ├── lower-id
│ │ ├── merged
│ │ │ ├── bin
│ │ │ ├── data
│ │ │ ├── dev
│ │ │ ├── etc
│ │ │ ├── home
│ │ │ ├── proc
│ │ │ ├── root
│ │ │ ├── sys
│ │ │ ├── tmp
│ │ │ ├── usr
│ │ │ └── var
│ │ ├── upper
│ │ │ ├── data
│ │ │ ├── dev
│ │ │ ├── etc
│ │ │ ├── proc
│ │ │ ├── root
│ │ │ └── sys
│ │ └── work
│ │ └── work
│ └── c1eb6f4be0f4f384fe4a1645cc03e3f9c3c81c72a9f276c844f62c6d7cca0974-init
│ ├── lower-id
│ ├── merged
│ ├── upper
│ │ ├── dev
│ │ ├── etc
│ │ ├── proc
│ │ └── sys
│ └── work
│ └── work
├── plugins
│ ├── storage
│ │ └── blobs
│ │ └── tmp
│ └── tmp
├── swarm
├── tmp
├── tmp-old
├── trust
└── volumes
└── metadata.db
93 directories, 22 files
在busybox内查看,注意 / 的mount,与上述粗红对应
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 |
/ # mount rootfs on / type rootfs (rw) overlay on / type overlay (rw,seclabel,relatime,lowerdir=/var/lib/docker/overlay/a626a89bd36ab93ba340eb98f01a824b1edb75082694cc8c695992b4e57e1087/root,upperdir=/var/lib/docker/overlay/c1eb6f4be0f4f384fe4a1645cc03e3f9c3c81c72a9f276c844f62c6d7cca0974/upper,workdir=/var/lib/docker/overlay/c1eb6f4be0f4f384fe4a1645cc03e3f9c3c81c72a9f276c844f62c6d7cca0974/work) proc on /proc type proc (rw,nosuid,nodev,noexec,relatime) tmpfs on /dev type tmpfs (rw,seclabel,nosuid,mode=755) devpts on /dev/pts type devpts (rw,seclabel,nosuid,noexec,relatime,gid=5,mode=620,ptmxmode=666) sysfs on /sys type sysfs (ro,seclabel,nosuid,nodev,noexec,relatime) tmpfs on /sys/fs/cgroup type tmpfs (ro,seclabel,nosuid,nodev,noexec,relatime,mode=755) cgroup on /sys/fs/cgroup/systemd type cgroup (ro,nosuid,nodev,noexec,relatime,xattr,release_agent=/usr/lib/systemd/systemd-cgroups-agent,name=systemd) cgroup on /sys/fs/cgroup/memory type cgroup (ro,nosuid,nodev,noexec,relatime,memory) cgroup on /sys/fs/cgroup/pids type cgroup (ro,nosuid,nodev,noexec,relatime,pids) cgroup on /sys/fs/cgroup/net_prio,net_cls type cgroup (ro,nosuid,nodev,noexec,relatime,net_prio,net_cls) cgroup on /sys/fs/cgroup/cpuset type cgroup (ro,nosuid,nodev,noexec,relatime,cpuset) cgroup on /sys/fs/cgroup/hugetlb type cgroup (ro,nosuid,nodev,noexec,relatime,hugetlb) cgroup on /sys/fs/cgroup/cpuacct,cpu type cgroup (ro,nosuid,nodev,noexec,relatime,cpuacct,cpu) cgroup on /sys/fs/cgroup/freezer type cgroup (ro,nosuid,nodev,noexec,relatime,freezer) cgroup on /sys/fs/cgroup/devices type cgroup (ro,nosuid,nodev,noexec,relatime,devices) cgroup on /sys/fs/cgroup/blkio type cgroup (ro,nosuid,nodev,noexec,relatime,blkio) cgroup on /sys/fs/cgroup/perf_event type cgroup (ro,nosuid,nodev,noexec,relatime,perf_event) mqueue on /dev/mqueue type mqueue (rw,seclabel,nosuid,nodev,noexec,relatime) /dev/mapper/centos-root on /data type xfs (rw,seclabel,relatime,attr2,inode64,noquota) /dev/mapper/centos-root on /etc/resolv.conf type xfs (rw,seclabel,relatime,attr2,inode64,noquota) /dev/mapper/centos-root on /etc/hostname type xfs (rw,seclabel,relatime,attr2,inode64,noquota) /dev/mapper/centos-root on /etc/hosts type xfs (rw,seclabel,relatime,attr2,inode64,noquota) shm on /dev/shm type tmpfs (rw,seclabel,nosuid,nodev,noexec,relatime,size=65536k) devpts on /dev/console type devpts (rw,seclabel,nosuid,noexec,relatime,gid=5,mode=620,ptmxmode=000) proc on /proc/asound type proc (ro,nosuid,nodev,noexec,relatime) proc on /proc/bus type proc (ro,nosuid,nodev,noexec,relatime) proc on /proc/fs type proc (ro,nosuid,nodev,noexec,relatime) proc on /proc/irq type proc (ro,nosuid,nodev,noexec,relatime) proc on /proc/sys type proc (ro,nosuid,nodev,noexec,relatime) proc on /proc/sysrq-trigger type proc (ro,nosuid,nodev,noexec,relatime) tmpfs on /proc/kcore type tmpfs (rw,seclabel,nosuid,mode=755) tmpfs on /proc/timer_list type tmpfs (rw,seclabel,nosuid,mode=755) tmpfs on /proc/timer_stats type tmpfs (rw,seclabel,nosuid,mode=755) tmpfs on /proc/sched_debug type tmpfs (rw,seclabel,nosuid,mode=755) tmpfs on /sys/firmware type tmpfs (ro,seclabel,relatime) / # df Filesystem 1K-blocks Used Available Use% Mounted on overlay 18307072 1672776 16634296 9% / tmpfs 2015208 0 2015208 0% /dev tmpfs 2015208 0 2015208 0% /sys/fs/cgroup /dev/mapper/centos-root 18307072 1672776 16634296 9% /data |
在宿主机的目录下创建一个文件,在容器里可以被看到:
|
1 2 3 4 5 |
[root@docker1 docker]# cd /root/dockervolume/ [root@docker1 dockervolume]# touch busybox.txt / # ls /data/ busybox.txt |
网络方面:
启动的busybox container使用一个veth pair 连接到了 docker0网桥上,从网桥对应的网络获得IP地址,系统默认启动了 icc。 从宿主机ifconfig角度看,多了一个veth接口,该接口即连接到了docker0网桥上。在busybox内部,看到正常的一个eth0,其实它是veth pair的另一端。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 |
[root@docker1 docker]# docker network ls NETWORK ID NAME DRIVER SCOPE 734c4df7548e bridge bridge local e7f32fd414b9 host host local 206ea33a6608 none null local [root@docker1 docker]# docker network inspect 734c4df7548e [ { "Name": "bridge", "Id": "734c4df7548e0b27980630a0edf4eec2094bfb24c51f8b89b04c543f7fd866b0", "Created": "2017-05-08T11:19:43.110067372+08:00", "Scope": "local", "Driver": "bridge", "EnableIPv6": false, "IPAM": { "Driver": "default", "Options": null, "Config": [ { "Subnet": "172.17.0.0/16", "Gateway": "172.17.0.1" } ] }, "Internal": false, "Attachable": false, "Ingress": false, "Containers": { "985e538f6b25487f5944707d44db1c3f624dd83f95adf02ab901fc75e6750823": { "Name": "awesome_torvalds", "EndpointID": "6c844510d4ab0ac7c98a33a9389438da87b05eb0a447d0d006f6fdb0a2105b3a", "MacAddress": "02:42:ac:11:00:02", "IPv4Address": "172.17.0.2/16", "IPv6Address": "" } }, "Options": { "com.docker.network.bridge.default_bridge": "true", "com.docker.network.bridge.enable_icc": "true", "com.docker.network.bridge.enable_ip_masquerade": "true", "com.docker.network.bridge.host_binding_ipv4": "0.0.0.0", "com.docker.network.bridge.name": "docker0", "com.docker.network.driver.mtu": "1500" }, "Labels": {} } ] |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 |
[root@docker1 docker]# ifconfig docker0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 172.17.0.1 netmask 255.255.0.0 broadcast 0.0.0.0 inet6 fe80::42:4eff:febe:c289 prefixlen 64 scopeid 0x20<link> ether 02:42:4e:be:c2:89 txqueuelen 0 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 2 bytes 168 (168.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 eno16777736: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.0.129 netmask 255.255.255.0 broadcast 192.168.0.255 inet6 fe80::20c:29ff:fe42:d98 prefixlen 64 scopeid 0x20<link> ether 00:0c:29:42:0d:98 txqueuelen 1000 (Ethernet) RX packets 25735 bytes 7140443 (6.8 MiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 6890 bytes 1759536 (1.6 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 eno33554960: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 ether 00:0c:29:42:0d:a2 txqueuelen 1000 (Ethernet) RX packets 233 bytes 42888 (41.8 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 eno50332184: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 ether 00:0c:29:42:0d:ac txqueuelen 1000 (Ethernet) RX packets 233 bytes 42888 (41.8 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1 (Local Loopback) RX packets 68 bytes 5844 (5.7 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 68 bytes 5844 (5.7 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 veth0524764: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet6 fe80::b05c:6aff:fe25:44fd prefixlen 64 scopeid 0x20<link> ether b2:5c:6a:25:44:fd txqueuelen 0 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 8 bytes 648 (648.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
/ # ifconfig eth0 Link encap:Ethernet HWaddr 02:42:AC:11:00:02 inet addr:172.17.0.2 Bcast:0.0.0.0 Mask:255.255.0.0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:8 errors:0 dropped:0 overruns:0 frame:0 TX packets:0 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:648 (648.0 B) TX bytes:0 (0.0 B) lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:0 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1 RX bytes:0 (0.0 B) TX bytes:0 (0.0 B) |
docker inspect 查看该容器,可以看到容器的几大部分配置,config, hostconfig, networksetting, graphdirver. hostconfig是与宿主机有关联的相关配置。 网络部分中的sandbox可以理解为容器的namespace,其内包含一个endpoint,连接到相关network上,类似下图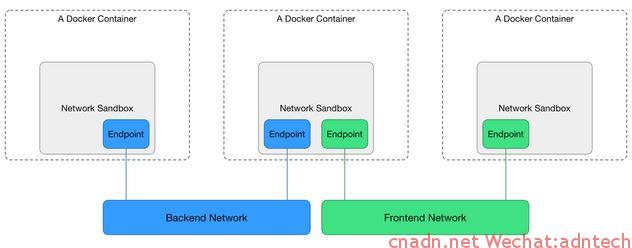
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 |
[root@docker1 ns]# docker inspect awesome_torvalds [ { "Id": "985e538f6b25487f5944707d44db1c3f624dd83f95adf02ab901fc75e6750823", "Created": "2017-05-09T01:26:23.01518301Z", "Path": "sh", "Args": [], "State": { "Status": "running", "Running": true, "Paused": false, "Restarting": false, "OOMKilled": false, "Dead": false, "Pid": 5013, "ExitCode": 0, "Error": "", "StartedAt": "2017-05-09T01:26:23.179898703Z", "FinishedAt": "0001-01-01T00:00:00Z" }, "Image": "sha256:00f017a8c2a6e1fe2ffd05c281f27d069d2a99323a8cd514dd35f228ba26d2ff", "ResolvConfPath": "/var/lib/docker/containers/985e538f6b25487f5944707d44db1c3f624dd83f95adf02ab901fc75e6750823/resolv.conf", "HostnamePath": "/var/lib/docker/containers/985e538f6b25487f5944707d44db1c3f624dd83f95adf02ab901fc75e6750823/hostname", "HostsPath": "/var/lib/docker/containers/985e538f6b25487f5944707d44db1c3f624dd83f95adf02ab901fc75e6750823/hosts", "LogPath": "/var/lib/docker/containers/985e538f6b25487f5944707d44db1c3f624dd83f95adf02ab901fc75e6750823/985e538f6b25487f5944707d44db1c3f624dd83f95adf02ab901fc75e6750823-json.log", "Name": "/awesome_torvalds", "RestartCount": 0, "Driver": "overlay", "MountLabel": "", "ProcessLabel": "", "AppArmorProfile": "", "ExecIDs": null, "HostConfig": { "Binds": [ "/root/dockervolume/:/data" ], "ContainerIDFile": "", "LogConfig": { "Type": "json-file", "Config": {} }, "NetworkMode": "default", "PortBindings": {}, "RestartPolicy": { "Name": "no", "MaximumRetryCount": 0 }, "AutoRemove": false, "VolumeDriver": "", "VolumesFrom": null, "CapAdd": null, "CapDrop": null, "Dns": [], "DnsOptions": [], "DnsSearch": [], "ExtraHosts": null, "GroupAdd": null, "IpcMode": "", "Cgroup": "", "Links": null, "OomScoreAdj": 0, "PidMode": "", "Privileged": false, "PublishAllPorts": false, "ReadonlyRootfs": false, "SecurityOpt": null, "UTSMode": "", "UsernsMode": "", "ShmSize": 67108864, "Runtime": "runc", "ConsoleSize": [ 0, 0 ], "Isolation": "", "CpuShares": 0, "Memory": 0, "NanoCpus": 0, "CgroupParent": "", "BlkioWeight": 0, "BlkioWeightDevice": null, "BlkioDeviceReadBps": null, "BlkioDeviceWriteBps": null, "BlkioDeviceReadIOps": null, "BlkioDeviceWriteIOps": null, "CpuPeriod": 0, "CpuQuota": 0, "CpuRealtimePeriod": 0, "CpuRealtimeRuntime": 0, "CpusetCpus": "", "CpusetMems": "", "Devices": [], "DeviceCgroupRules": null, "DiskQuota": 0, "KernelMemory": 0, "MemoryReservation": 0, "MemorySwap": 0, "MemorySwappiness": -1, "OomKillDisable": false, "PidsLimit": 0, "Ulimits": null, "CpuCount": 0, "CpuPercent": 0, "IOMaximumIOps": 0, "IOMaximumBandwidth": 0 }, "GraphDriver": { "Data": { "LowerDir": "/var/lib/docker/overlay/a626a89bd36ab93ba340eb98f01a824b1edb75082694cc8c695992b4e57e1087/root", "MergedDir": "/var/lib/docker/overlay/c1eb6f4be0f4f384fe4a1645cc03e3f9c3c81c72a9f276c844f62c6d7cca0974/merged", "UpperDir": "/var/lib/docker/overlay/c1eb6f4be0f4f384fe4a1645cc03e3f9c3c81c72a9f276c844f62c6d7cca0974/upper", "WorkDir": "/var/lib/docker/overlay/c1eb6f4be0f4f384fe4a1645cc03e3f9c3c81c72a9f276c844f62c6d7cca0974/work" }, "Name": "overlay" }, "Mounts": [ { "Type": "bind", "Source": "/root/dockervolume", "Destination": "/data", "Mode": "", "RW": true, "Propagation": "" } ], "Config": { "Hostname": "985e538f6b25", "Domainname": "", "User": "", "AttachStdin": true, "AttachStdout": true, "AttachStderr": true, "Tty": true, "OpenStdin": true, "StdinOnce": true, "Env": [ "PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin" ], "Cmd": [ "sh" ], "Image": "busybox", "Volumes": null, "WorkingDir": "", "Entrypoint": null, "OnBuild": null, "Labels": {} }, "NetworkSettings": { "Bridge": "", "SandboxID": "3a98bfe3abf762a396cdf403eaa1fa3d7aa2b26473a40f5797c6e9020ca0e055", "HairpinMode": false, "LinkLocalIPv6Address": "", "LinkLocalIPv6PrefixLen": 0, "Ports": {}, "SandboxKey": "/var/run/docker/netns/3a98bfe3abf7", "SecondaryIPAddresses": null, "SecondaryIPv6Addresses": null, "EndpointID": "6c844510d4ab0ac7c98a33a9389438da87b05eb0a447d0d006f6fdb0a2105b3a", "Gateway": "172.17.0.1", "GlobalIPv6Address": "", "GlobalIPv6PrefixLen": 0, "IPAddress": "172.17.0.2", "IPPrefixLen": 16, "IPv6Gateway": "", "MacAddress": "02:42:ac:11:00:02", "Networks": { "bridge": { "IPAMConfig": null, "Links": null, "Aliases": null, "NetworkID": "734c4df7548e0b27980630a0edf4eec2094bfb24c51f8b89b04c543f7fd866b0", "EndpointID": "6c844510d4ab0ac7c98a33a9389438da87b05eb0a447d0d006f6fdb0a2105b3a", "Gateway": "172.17.0.1", "IPAddress": "172.17.0.2", "IPPrefixLen": 16, "IPv6Gateway": "", "GlobalIPv6Address": "", "GlobalIPv6PrefixLen": 0, "MacAddress": "02:42:ac:11:00:02" } } } } ] |
那么如何在宿主机下进入该容器的namespace里面呢?
1. 首先通过上述输出中的State.Pid获得该容器在主机里的进程号,这里是5013
2. 将/proc/5013/ns/net link到/var/run/netns下,例如
|
1 |
[root@docker1 ns]# ln -s /proc/5013/ns/net /var/run/netns/busyboxns |
随后就可以模拟进入该ns下查看:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
[root@docker1 ns]# ip netns exec busyboxns ifconfig eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 172.17.0.2 netmask 255.255.0.0 broadcast 0.0.0.0 ether 02:42:ac:11:00:02 txqueuelen 0 (Ethernet) RX packets 15 bytes 1222 (1.1 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 7 bytes 574 (574.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 loop txqueuelen 1 (Local Loopback) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 |
docker run -itd 方式运行一个带sh的容器后,再次docker attach上去后并exit退出bash,此时这个容器会被stop,用docker exec -it *** sh执行后再退出则不会stop之前运行的容器,因为此时后一个命令,相当于又开了一个新进程,原来运行该容器的进程还活着
docker start命令启动的container,依旧包含有使用run命令时候所带的参数。
映射主机8080到容器的80端口后,iptables变化,可以看到多了一条目的地址/PAT转换的规则,以及多了一条接受目的地址是容器,目的端口是80的接受规则(注意match参数都是tcp)
-A DOCKER -d 172.17.0.3/32 ! -i docker0 -o docker0 -p tcp -m tcp --dport 80 -j ACCEPT
控制的是容许从宿主机外部过来的请求,input 接口是非docker0,无此规则的话将只能从宿主机本身发起到容器的访问
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
[root@docker1 494d881fa57ffb2f1cf77861aa208c22385e9abb43bf03201d41aa6e42167f51]# iptables-save | grep -i docker :DOCKER - [0:0] -A PREROUTING -m addrtype --dst-type LOCAL -j DOCKER -A OUTPUT ! -d 127.0.0.0/8 -m addrtype --dst-type LOCAL -j DOCKER -A POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE -A DOCKER -i docker0 -j RETURN -A DOCKER ! -i docker0 -p tcp -m tcp --dport 8080 -j DNAT --to-destination 172.17.0.3:80 :DOCKER - [0:0] :DOCKER-ISOLATION - [0:0] -A FORWARD -j DOCKER-ISOLATION -A FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A FORWARD -o docker0 -j DOCKER -A FORWARD -i docker0 ! -o docker0 -j ACCEPT -A FORWARD -i docker0 -o docker0 -j ACCEPT -A DOCKER -d 172.17.0.3/32 ! -i docker0 -o docker0 -p tcp -m tcp --dport 80 -j ACCEPT -A DOCKER-ISOLATION -j RETURN |
