Host网络方式:
容器run的时候启用--network来指明host网络类型,使得容器复用host的网络空间。容器将得到和宿主机一样的网络接口及IP。这样的缺点是容器在网络上没有隔离,而且多个容器存在抢占同一端口的可能性,限制性比较大。
桥接外部网络方式:
容器桥接到一个自定义网桥(非docker产生的网桥,而是linux中独立创建的网桥),并将该自定义网桥与宿主机物理接口进行桥接,这样将容器直接透传到外部物理网络里来,使得各个容器就像直接活在外部网络中的一个主机一样。可以通过pipework这个工具来自动化执行上述这个过程
|
1 2 3 4 5 6 7 8 9 10 |
[root@localhost ~]# pipework br0 busybox1 192.168.188.188@192.168.188.1 Error: No such object: busybox1 [root@localhost ~]# docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES [root@localhost ~]# docker run -itd --name busybox1 busybox 0935decc0af78254f4ec446e4dc25a50dc5d135d517edf5da39e6a7e61511519 [root@localhost ~]# pipework br0 busybox1 192.168.188.188/24@192.168.188.1 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 |
[root@localhost ~]# ifconfig br0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet6 fe80::b496:f0ff:fe56:845a prefixlen 64 scopeid 0x20<link> ether b6:96:f0:56:84:5a txqueuelen 0 (Ethernet) RX packets 4 bytes 112 (112.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 9 bytes 738 (738.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 docker0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 172.17.0.1 netmask 255.255.0.0 broadcast 0.0.0.0 inet6 fe80::42:b7ff:fef7:ea61 prefixlen 64 scopeid 0x20<link> ether 02:42:b7:f7:ea:61 txqueuelen 0 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 3 bytes 258 (258.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 eno16777736: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.0.183 netmask 255.255.255.0 broadcast 192.168.0.255 inet6 fe80::20c:29ff:feae:1179 prefixlen 64 scopeid 0x20<link> ether 00:0c:29:ae:11:79 txqueuelen 1000 (Ethernet) RX packets 251156 bytes 305142445 (291.0 MiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 85054 bytes 5898472 (5.6 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 eno33554960: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 ether 00:0c:29:ae:11:83 txqueuelen 1000 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 eno50332184: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 ether 00:0c:29:ae:11:8d txqueuelen 1000 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 0 (Local Loopback) RX packets 4 bytes 340 (340.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 4 bytes 340 (340.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 veth1452d20: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet6 fe80::2092:b4ff:feda:c102 prefixlen 64 scopeid 0x20<link> ether 22:92:b4:da:c1:02 txqueuelen 0 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 8 bytes 648 (648.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 veth1pl70825: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet6 fe80::b496:f0ff:fe56:845a prefixlen 64 scopeid 0x20<link> ether b6:96:f0:56:84:5a txqueuelen 1000 (Ethernet) RX packets 4 bytes 168 (168.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 15 bytes 1206 (1.1 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
[root@localhost ~]# ethtool -S veth1pl70825 NIC statistics: peer_ifindex: 14 [root@localhost ~]# ip link 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 2: eno16777736: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP mode DEFAULT qlen 1000 link/ether 00:0c:29:ae:11:79 brd ff:ff:ff:ff:ff:ff 3: eno33554960: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP mode DEFAULT qlen 1000 link/ether 00:0c:29:ae:11:83 brd ff:ff:ff:ff:ff:ff 4: eno50332184: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP mode DEFAULT qlen 1000 link/ether 00:0c:29:ae:11:8d brd ff:ff:ff:ff:ff:ff 5: ovs-system: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN mode DEFAULT link/ether 8e:ed:03:83:45:0b brd ff:ff:ff:ff:ff:ff 6: br-int: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN mode DEFAULT link/ether e2:2e:3f:25:e0:40 brd ff:ff:ff:ff:ff:ff 7: br-ex: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN mode DEFAULT link/ether be:22:2e:ad:d8:48 brd ff:ff:ff:ff:ff:ff 8: docker0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP mode DEFAULT link/ether 02:42:b7:f7:ea:61 brd ff:ff:ff:ff:ff:ff 12: veth1452d20@if11: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master docker0 state UP mode DEFAULT link/ether 22:92:b4:da:c1:02 brd ff:ff:ff:ff:ff:ff link-netnsid 0 13: br0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP mode DEFAULT link/ether b6:96:f0:56:84:5a brd ff:ff:ff:ff:ff:ff 15: veth1pl70825@if14: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master br0 state UP mode DEFAULT qlen 1000 link/ether b6:96:f0:56:84:5a brd ff:ff:ff:ff:ff:ff link-netnsid 0 [root@localhost ~]# docker ps a |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
[root@localhost ~]# linkns The script will link all running containers namespace into /var/run/netns, so you can use ip netns command for them. Deleting all existed symbol links namespace for busybox1 was linked into /var/run/netns/busybox1 [root@localhost ~]# ip netns busybox1 ip link Command "busybox1" is unknown, try "ip netns help". [root@localhost ~]# ip netns exec busybox1 ip link 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 11: eth0@if12: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP mode DEFAULT link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff link-netnsid 0 14: eth1@if15: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP mode DEFAULT qlen 1000 link/ether da:9b:43:80:73:09 brd ff:ff:ff:ff:ff:ff link-netnsid 0 |
可以看到pipework自动为运行中的容器增加了新网卡eth1并配置IP及路由,同时将该容器内网卡命名为eth1并link到外部一个veth上,该veth落在br0上. 在容器内部删除其它缺省路由,根据命令里提供的网关地址设置缺省路由。
|
1 2 3 4 5 6 |
[root@localhost ~]# brctl show bridge name bridge id STP enabled interfaces br0 8000.b696f056845a no veth1pl70825 veth1pl71141 docker0 8000.0242b7f7ea61 no veth1452d20 vethc2954fd |
|
1 2 3 4 5 6 7 |
/ # route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 192.168.188.1 0.0.0.0 UG 0 0 0 eth1 172.17.0.0 0.0.0.0 255.255.0.0 U 0 0 0 eth0 192.168.188.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1 / # |
pipework并没有对br0配置接口IP,也没有将其桥接到物理网卡上,这一步工作还需手工完成,将eno33554960加入到br0网桥,且配置br0的IP地址:
|
1 2 3 4 5 6 7 8 |
br0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.188.1 netmask 255.255.255.0 broadcast 192.168.188.255 inet6 fe80::b496:f0ff:fe56:845a prefixlen 64 scopeid 0x20<link> ether f6:8d:63:4a:6b:46 txqueuelen 0 (Ethernet) RX packets 86 bytes 2576 (2.5 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 18 bytes 1884 (1.8 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 |
|
1 2 3 4 5 6 7 8 9 10 |
[root@localhost ~]# brctl addif br0 eno33554960 [root@localhost ~]# [root@localhost ~]# [root@localhost ~]# brctl show bridge name bridge id STP enabled interfaces br0 8000.000c29ae1183 no eno33554960 veth1pl71474 veth1pl71688 docker0 8000.0242b7f7ea61 no veth2d6e851 veth5082a15 |
在容器内ping 网关,及外部地址:
|
1 2 3 4 5 6 7 8 9 10 11 12 |
/ # ping 192.168.188.1 PING 192.168.188.1 (192.168.188.1): 56 data bytes 64 bytes from 192.168.188.1: seq=0 ttl=64 time=0.281 ms 64 bytes from 192.168.188.1: seq=1 ttl=64 time=0.136 ms ^C --- 192.168.188.1 ping statistics --- 2 packets transmitted, 2 packets received, 0% packet loss round-trip min/avg/max = 0.136/0.208/0.281 ms / # ping 8.8.8.8 PING 8.8.8.8 (8.8.8.8): 56 data bytes 64 bytes from 8.8.8.8: seq=1 ttl=128 time=306.267 ms 64 bytes from 8.8.8.8: seq=2 ttl=128 time=245.188 ms |
备注:上述方法执行的pipework 默认并没有保存到容器里,容器重启后配置都会丢失,在一个生产环境下从容器本身这种结构考虑,一般不应该考虑为容器设置内部直接设置固定IP,因此对于上述方法用起来还是比较麻烦的,每次启动容器后,需要根据命名自动执行相关pipework命令,这时候如何保证服务发现,以及确保IP分配不冲突,对于某些依赖服务还需考虑提供恒定的IP。另外,在这种结构下,所有容器之间都在一个二层,容器间通信控制本身需要外部来维护控制。 docker commit是不会保存这种网络接口增加变化的。
在另一台主机上执行同样类似的操作过程,随后不同主机上的容器即可以相互通信:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
/ # route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 192.168.188.1 0.0.0.0 UG 0 0 0 eth1 172.17.0.0 0.0.0.0 255.255.0.0 U 0 0 0 eth0 192.168.188.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1 / # ifconfig eth0 Link encap:Ethernet HWaddr 02:42:AC:11:00:05 inet addr:172.17.0.5 Bcast:0.0.0.0 Mask:255.255.0.0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:8 errors:0 dropped:0 overruns:0 frame:0 TX packets:0 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:648 (648.0 B) TX bytes:0 (0.0 B) eth1 Link encap:Ethernet HWaddr DE:98:6D:59:BC:47 inet addr:192.168.188.199 Bcast:192.168.188.255 Mask:255.255.255.0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:345 errors:0 dropped:0 overruns:0 frame:0 TX packets:58 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:21302 (20.8 KiB) TX bytes:5012 (4.8 KiB) lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:4 errors:0 dropped:0 overruns:0 frame:0 TX packets:4 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1 RX bytes:448 (448.0 B) TX bytes:448 (448.0 B) / # ping 192.168.188.189 PING 192.168.188.189 (192.168.188.189): 56 data bytes 64 bytes from 192.168.188.189: seq=0 ttl=64 time=0.654 ms 64 bytes from 192.168.188.189: seq=1 ttl=64 time=0.770 ms |
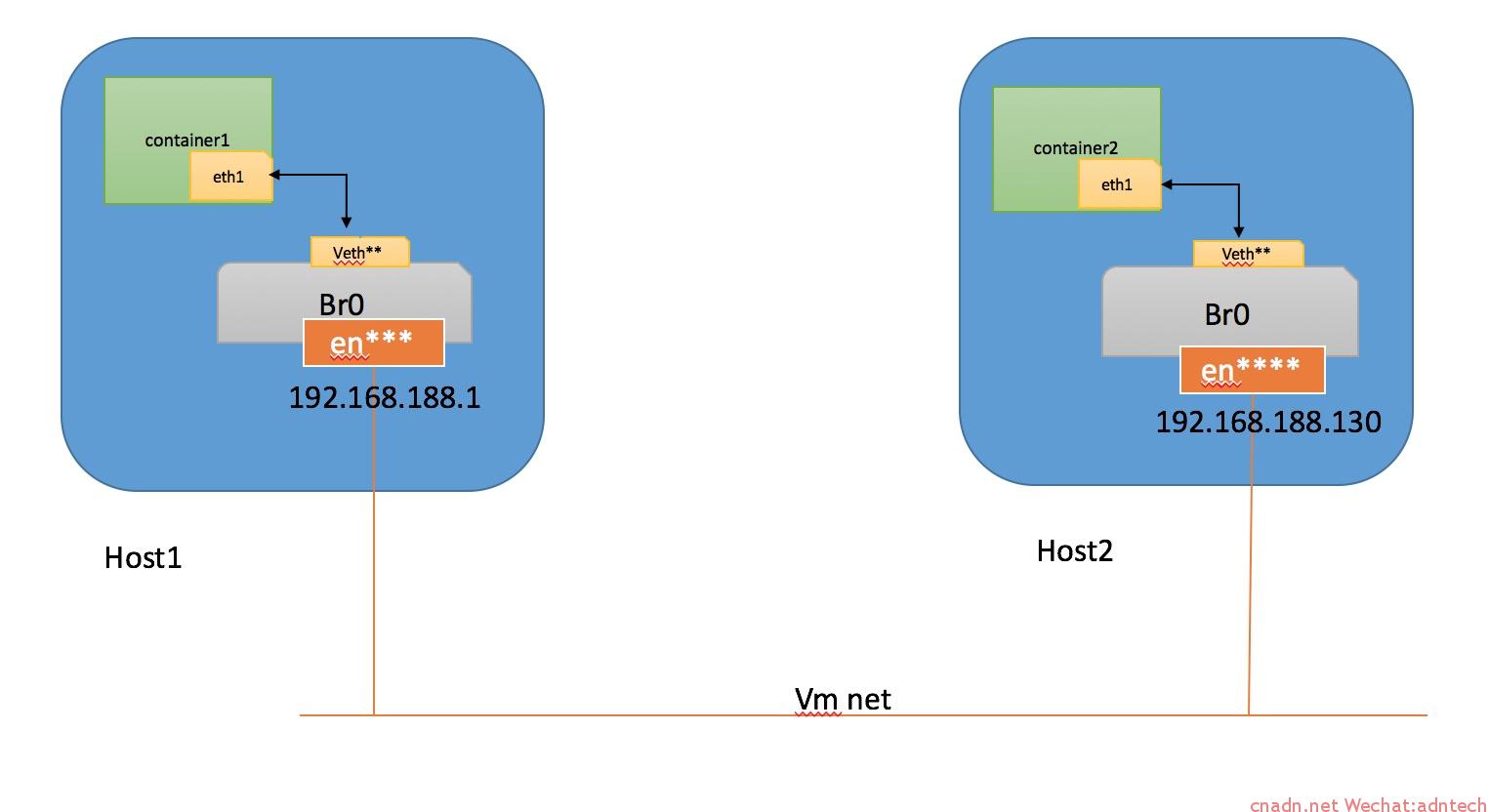
容器目的地外网ip的通讯,数据包发给br0接口,br0接口在host中,再次查找主机路由表,将数据包路由出去。注意两台宿主机br0接口地址不一样,每个宿主机容器的网关指向本宿主机的br0的IP。 网络结构如下:
在整个上述配置中,所有配置都未写入文件,重启容器,重启主机相关配置都会丢失。对于容器可考虑结合自动化脚本在启动容器后执行相关pipework工作,而对于主机桥接网络,实际上建议配置具体的br0接口文件,将IP以及桥接的物理接口固定配置在文件里(类似编辑一个接口网络配置文件一样)
而如果不想通过pipework来做,则可以考虑新建br0后,修改docker daemon的缺省启动参数来使得容器run的时候默认绑定到这个br0 bridge网络上,同时将一个宿主物理网卡加入到该br0实现直接桥接到外部网络. 缺省启动文件 /usr/lib/systemd/system/docker.service 相关启动参数包含:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 |
[root@localhost sysconfig]# dockerd -h Flag shorthand -h has been deprecated, please use --help Usage: dockerd COMMAND A self-sufficient runtime for containers. Options: --add-runtime runtime Register an additional OCI compatible runtime (default []) --api-cors-header string Set CORS headers in the Engine API --authorization-plugin list Authorization plugins to load --bip string Specify network bridge IP -b, --bridge string Attach containers to a network bridge --cgroup-parent string Set parent cgroup for all containers --cluster-advertise string Address or interface name to advertise --cluster-store string URL of the distributed storage backend --cluster-store-opt map Set cluster store options (default map[]) --config-file string Daemon configuration file (default "/etc/docker/daemon.json") --containerd string Path to containerd socket --cpu-rt-period int Limit the CPU real-time period in microseconds --cpu-rt-runtime int Limit the CPU real-time runtime in microseconds --data-root string Root directory of persistent Docker state (default "/var/lib/docker") -D, --debug Enable debug mode --default-gateway ip Container default gateway IPv4 address --default-gateway-v6 ip Container default gateway IPv6 address --default-runtime string Default OCI runtime for containers (default "runc") --default-shm-size bytes Default shm size for containers (default 64MiB) --default-ulimit ulimit Default ulimits for containers (default []) --disable-legacy-registry Disable contacting legacy registries --dns list DNS server to use --dns-opt list DNS options to use --dns-search list DNS search domains to use --exec-opt list Runtime execution options --exec-root string Root directory for execution state files (default "/var/run/docker") --experimental Enable experimental features --fixed-cidr string IPv4 subnet for fixed IPs --fixed-cidr-v6 string IPv6 subnet for fixed IPs -G, --group string Group for the unix socket (default "docker") --help Print usage -H, --host list Daemon socket(s) to connect to --icc Enable inter-container communication (default true) --init Run an init in the container to forward signals and reap processes --init-path string Path to the docker-init binary --insecure-registry list Enable insecure registry communication --ip ip Default IP when binding container ports (default 0.0.0.0) --ip-forward Enable net.ipv4.ip_forward (default true) --ip-masq Enable IP masquerading (default true) --iptables Enable addition of iptables rules (default true) --ipv6 Enable IPv6 networking --label list Set key=value labels to the daemon --live-restore Enable live restore of docker when containers are still running --log-driver string Default driver for container logs (default "json-file") -l, --log-level string Set the logging level ("debug"|"info"|"warn"|"error"|"fatal") (default "info") --log-opt map Default log driver options for containers (default map[]) --max-concurrent-downloads int Set the max concurrent downloads for each pull (default 3) --max-concurrent-uploads int Set the max concurrent uploads for each push (default 5) --metrics-addr string Set default address and port to serve the metrics api on --mtu int Set the containers network MTU --oom-score-adjust int Set the oom_score_adj for the daemon (default -500) -p, --pidfile string Path to use for daemon PID file (default "/var/run/docker.pid") --raw-logs Full timestamps without ANSI coloring --registry-mirror list Preferred Docker registry mirror --seccomp-profile string Path to seccomp profile --selinux-enabled Enable selinux support --shutdown-timeout int Set the default shutdown timeout (default 15) -s, --storage-driver string Storage driver to use --storage-opt list Storage driver options --swarm-default-advertise-addr string Set default address or interface for swarm advertised address --tls Use TLS; implied by --tlsverify --tlscacert string Trust certs signed only by this CA (default "/root/.docker/ca.pem") --tlscert string Path to TLS certificate file (default "/root/.docker/cert.pem") --tlskey string Path to TLS key file (default "/root/.docker/key.pem") --tlsverify Use TLS and verify the remote --userland-proxy Use userland proxy for loopback traffic (default true) --userland-proxy-path string Path to the userland proxy binary --userns-remap string User/Group setting for user namespaces -v, --version Print version information and quit |
注意:在centos7下,上述桥接后,还需要在主机iptables的FORWARD链中增加相关容许条目。例如:
iptables -I FORWARD 10 -s 0.0.0.0/0 -d 0.0.0.0/0 -j ACCEPT
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 |
[root@docker1 bin]# iptables -nL -v Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 107K 67M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 609 198K ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 78306 35M INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 75124 35M INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 75124 35M INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 28 1276 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 75071 35M REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 29765 2443K DOCKER-ISOLATION all -- * * 0.0.0.0/0 0.0.0.0/0 8 672 ACCEPT all -- * br-2aeddaf04b59 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 168 DOCKER all -- * br-2aeddaf04b59 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- br-2aeddaf04b59 !br-2aeddaf04b59 0.0.0.0/0 0.0.0.0/0 2 168 ACCEPT all -- br-2aeddaf04b59 br-2aeddaf04b59 0.0.0.0/0 0.0.0.0/0 32728 27M ACCEPT all -- * docker0 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 252 73164 DOCKER all -- * docker0 0.0.0.0/0 0.0.0.0/0 25842 1685K ACCEPT all -- docker0 !docker0 0.0.0.0/0 0.0.0.0/0 219 71052 ACCEPT all -- docker0 docker0 0.0.0.0/0 0.0.0.0/0 314 45736 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 14 1176 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 459 93682 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 459 93682 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 459 93682 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 368 87370 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 368 87370 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 368 87370 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 1599 packets, 471K bytes) pkts bytes target prot opt in out source destination 69898 13M OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain DOCKER (2 references) pkts bytes target prot opt in out source destination 12 768 ACCEPT tcp -- !docker0 docker0 0.0.0.0/0 172.17.0.3 tcp dpt:80 Chain DOCKER-ISOLATION (1 references) pkts bytes target prot opt in out source destination 0 0 DROP all -- docker0 br-2aeddaf04b59 0.0.0.0/0 0.0.0.0/0 0 0 DROP all -- br-2aeddaf04b59 docker0 0.0.0.0/0 0.0.0.0/0 59613 29M RETURN all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_IN_ZONES (1 references) pkts bytes target prot opt in out source destination 0 0 FWDI_public all -- eno16777736 * 0.0.0.0/0 0.0.0.0/0 [goto] 453 93298 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) pkts bytes target prot opt in out source destination Chain FORWARD_OUT_ZONES (1 references) pkts bytes target prot opt in out source destination 0 0 FWDO_public all -- * eno16777736 0.0.0.0/0 0.0.0.0/0 [goto] 368 87370 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) pkts bytes target prot opt in out source destination Chain FORWARD_direct (1 references) pkts bytes target prot opt in out source destination Chain FWDI_public (2 references) pkts bytes target prot opt in out source destination 459 93682 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 459 93682 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 459 93682 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 91 6312 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDI_public_allow (1 references) pkts bytes target prot opt in out source destination Chain FWDI_public_deny (1 references) pkts bytes target prot opt in out source destination Chain FWDI_public_log (1 references) pkts bytes target prot opt in out source destination Chain FWDO_public (2 references) pkts bytes target prot opt in out source destination 368 87370 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 368 87370 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 368 87370 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDO_public_allow (1 references) pkts bytes target prot opt in out source destination Chain FWDO_public_deny (1 references) pkts bytes target prot opt in out source destination Chain FWDO_public_log (1 references) pkts bytes target prot opt in out source destination Chain INPUT_ZONES (1 references) pkts bytes target prot opt in out source destination 56999 25M IN_public all -- eno16777736 * 0.0.0.0/0 0.0.0.0/0 [goto] 378 104K IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain INPUT_ZONES_SOURCE (1 references) pkts bytes target prot opt in out source destination Chain INPUT_direct (1 references) pkts bytes target prot opt in out source destination 3182 399K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 Chain IN_public (2 references) pkts bytes target prot opt in out source destination 75124 35M IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 75124 35M IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 75124 35M IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 7 552 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain IN_public_allow (1 references) pkts bytes target prot opt in out source destination 4 256 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW 14 892 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 ctstate NEW Chain IN_public_deny (1 references) pkts bytes target prot opt in out source destination Chain IN_public_log (1 references) pkts bytes target prot opt in out source destination Chain OUTPUT_direct (1 references) pkts bytes target prot opt in out source destination |
- 路由方式互联跨宿主机容器:
《《《见下一篇文章》》》